If you are using Linux as your host operating system and running VMware GSX Server virtual machines with host-only networking, IP masquerade gives you a convenient way to connect those virtual machines to the Internet. (IP masquerade also works with virtual machines that use bridged networking.)
To set up IP masquerading for virtual machines:
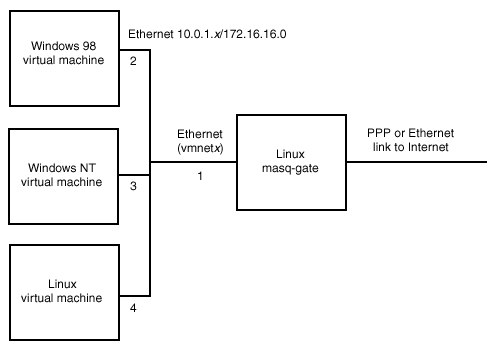
The network you set up looks like the following diagram.

The following table lists the options you should enable when compiling your Linux kernel.
|
Compile option |
Description |
Linux 2.2.x |
Linux 2.0.x |
|
CONFIG_EXPERIMENTAL |
Allows you to select experimental IP Masquerade code compiled into the kernel. |
Required |
Required |
|
CONFIG_MODULES |
Allows you to load ipmasq modules such as ip_masq_ftp.o. |
Required |
Required |
|
CONFIG_NET |
Provides networking support. |
Required |
Required |
|
CONFIG_FIREWALL |
Provides network firewall support. |
Required |
Required |
|
CONFIG_INET |
Provides TCP/IP networking. |
Required |
Required |
|
CONFIG_IP_FORWARD |
Provides IP forwarding and gateway capabilities. |
Required |
Required |
|
CONFIG_IP_FIREWALL |
Provides IP firewall support. |
Required |
Required |
|
CONFIG_IP_MASQUERADE |
Provides support for IP masquerading. |
Required |
Required |
|
CONFIG_IP_MASQUERADE_IPPORTFW |
Provides support for IP port forwarding. |
Recommended |
N/A |
|
CONFIG_IP_MASQUERADE_IPAUTOFW |
Provides support for automated IP forwarding during masquerading. |
Optional |
Required |
|
CONFIG_IP_MASQUERADE_ICMP |
Provides support for masquerading ICMP packets. |
Recommended |
Optional |
|
CONFIG_IP_ALWAYS_DEFRAG |
Provides support for defragmenting. |
Highly recommended |
Highly recommended |
|
CONFIG_DUMMY |
Provides support for the dummy net driver. |
Recommended |
Recommended |
|
CONFIG_IP_MASQUERADE_MFW |
Provides support for ip fwmark masq-forwarding. |
Optional |
N/A |
Note: These are just the components you need for IP masquerade. You also need to select various options in other categories to support your specific setup.
After compiling the kernel, you should compile and install the modules:
make modules; make modules_install
Then you should add a few lines to your /etc/rc.d/rc.local file (or another appropriate configuration file) to load the required modules from /lib/modules/2.x.x/ipv4/ automatically during each reboot:
.Reboot the Linux machine.
To configure your host system, you must perform these steps:
Setting up a generic network for the virtual machines
For this example, if your virtual machines are configured for host-only networking, you can identify the network address range by looking in the file /etc/vmware/config and finding the line that starts with vmnet1.HostOnlyAddress=. In the following example, the number there is 172.16.16.1. You then need to add entries in the following format in your /etc/hosts file:
127.0.0.1 localhost localhost.localdomain
172.16.16.2 win95 win95.linuxbogus.com
172.16.16.3 winnt winnt.linuxbogus.com
172.16.16.4 linux linux.linuxbogus.com
172.16.16.5 bsd bsd.linuxbogus.com
If your virtual machines are configured for bridged networking:
IP Address: 10.0.1.1/5 Subnet 255.255.255.0
You should follow this format when editing the /etc/hosts file:
127.0.0.1 localhost localhost.localdomain
10.0.1.1 gateway gateway.linuxbogus.com
10.0.1.2 win95 win95.linuxbogus.com
10.0.1.3 winnt winnt.linuxbogus.com
10.0.1.4 linux linux.linuxbogus.com
10.0.1.5 bsd bsd.linuxbogus.com
Note: If you run a name service, you should not add these machines into your DNS files.
Editing configuration files on SuSE Linux 6.2
On SuSE Linux 6.2, you must edit the /etc/rc.config file to use firewall and IP masquerade. The relevant lines for the configuration are shown next:
Note: The backslash character (\) indicates that the line in the script should continue without a line break. Do not type the backslash character.
# # Firewall settings - See /usr/doc/packages/firewall # for a detailed description # FW_START="yes" FW_LOCALNETS="192.168.2.0/24" FW_FTPSERVER="" FW_WWWSERVER="" FW_SSLSERVER="" FW_SSLPORT="443" FW_MAILSERVER="" FW_DNSSERVER="" FW_NNTPSERVER="" FW_NEWSFEED="" FW_WORLD_DEV="tr0" FW_INT_DEV="vmnet1" FW_LOG_ACCEPT="no" FW_LOG_DENY="yes" FW_ROUTER="192.168.2.0/24" FW_FRIENDS="no" FW_INOUT="yes" FW_SSH="no" FW_TRANSPROXY_OUT="" FW_TRANSPROXY_IN="" FW_REDIRECT="" FW_TCP_LOCKED_PORTS="1:1023" FW_UDP_LOCKED_PORTS="1:1023" # # Masquerading settings - See /usr/doc/packages/firewall # for a detailed description # MSQ_START="yes" MSQ_NETWORKS="192.168.2.0/24" MSQ_DEV="tr0" MSQ_MODULES="ip_masq_cuseeme ip_masq_ftp ip_masq_irc ip_masq_quake \ ip_masq_raudio ip_masq_vdolive"
Making appropriate firewall settings
SuSE Linux 6.2 installs a firewall init script in the directory /sbin/init.d. To be sure that the init script is run automatically whenever your reboot your SuSE host, do the following:
This command should return a list. As you may have noticed, the services listed in the command are for both run level 2 and run level 3 and are symbolic links to the /sbin/init.d/firewall init script.
Red Hat Linux 6.1 should install a firewall init script in the directory /etc/rc.d/init.d. If not, you may create one named firewall.rh.
You must also create a new file on Red Hat Linux hosts to enable the host to use firewall and IP masquerade.
To be sure that the init script is run automatically whenever you reboot your Red Hat Linux host:
Next, you need to run ipchains. For 2.2.x kernels and host-only networking, the commands would look like this:
ipchains -P forward DENY
ipchains -A forward -s 172.16.16.2/24 -j MASQ
or
ipchains -P forward DENY
ipchains -A forward -s 172.16.16.2/255.255.255.0 -j MASQ
If you are using bridged networking, in a terminal window type:
ipchains -P forward DENY
ipchains -A forward -s 10.0.1.0/24 -j MASQ
or
ipchains -P forward DENY
ipchains -A forward -s 10.0.1.0/255.255.255.0 -j MASQ
This applies to the whole subnet. You can do it on a per machine basis if you prefer. For example, if you are using bridged networking, type:
ipchains -P forward DENY
ipchains -A forward -s 10.0.1.2/32 -j MASQ
ipchains -A forward -s 10.0.1.5/32 -j MASQ
For 2.0.x kernels and bridged networking, in a terminal window type:
ipfwadm -F -p deny
ipfwadm -F -a m -S 10.0.1.0/24 -D 0.0.0.0/0
Note: ipfwadm is broken in the 2.2.x kernels. You must update to ipchains.
Warning: Do not make masquerading your default policy. If you do, someone who can manipulate his or her routing can tunnel straight back through your gateway, using it to masquerade their identity!
Perform the network installation the same way you would if you were trying to connect to a real network.
Note: Be sure that vmnet0, vmnet-bridge and so on are loaded properly.
Windows 95 or Windows 98
The procedure was successful if you can ping the virtual machine.
Windows NT 4.0
The procedure is successful if you can ping the virtual machine.
For more information, refer to the Linux IP Masquerade HOWTO ( http://www.linuxdoc.org/HOWTO/IP-Masquerade-HOWTO.html).
© 2001-2002 VMware, Inc. All rights reserved.